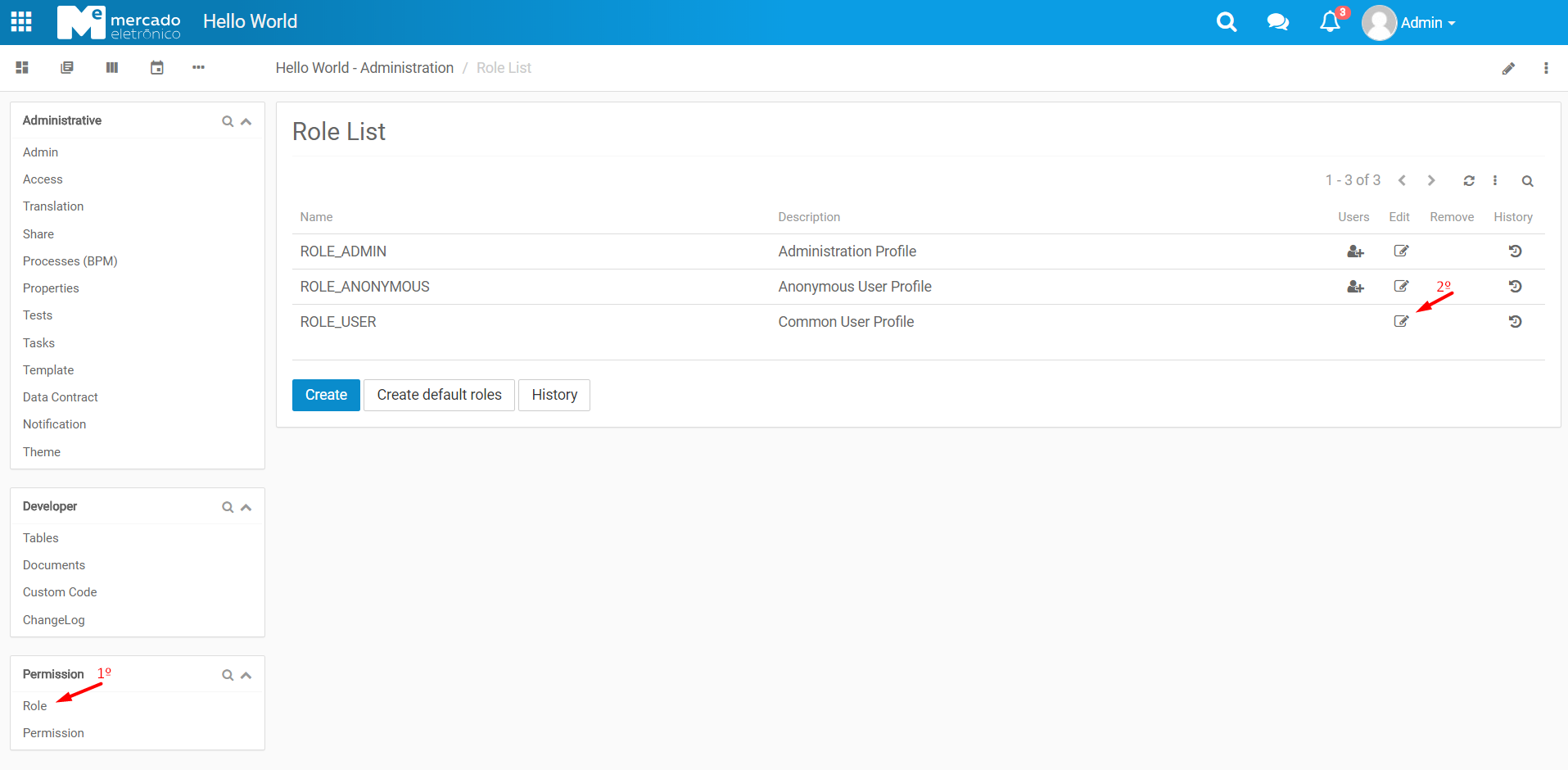
Roles
We can say that the rule works as if it were a 'profile', a role can have many permissions. Currently there are System Functions: ADMIN, USER and ANONYMOUS, within each Role we can have as many Permissions as we want.
Permissions
Permissions are defined inside the Roles, so we can have multiple users with a Role and within that Role add the necessary permissions.
- Example of the Roles and Permissions at Screens of the Application:
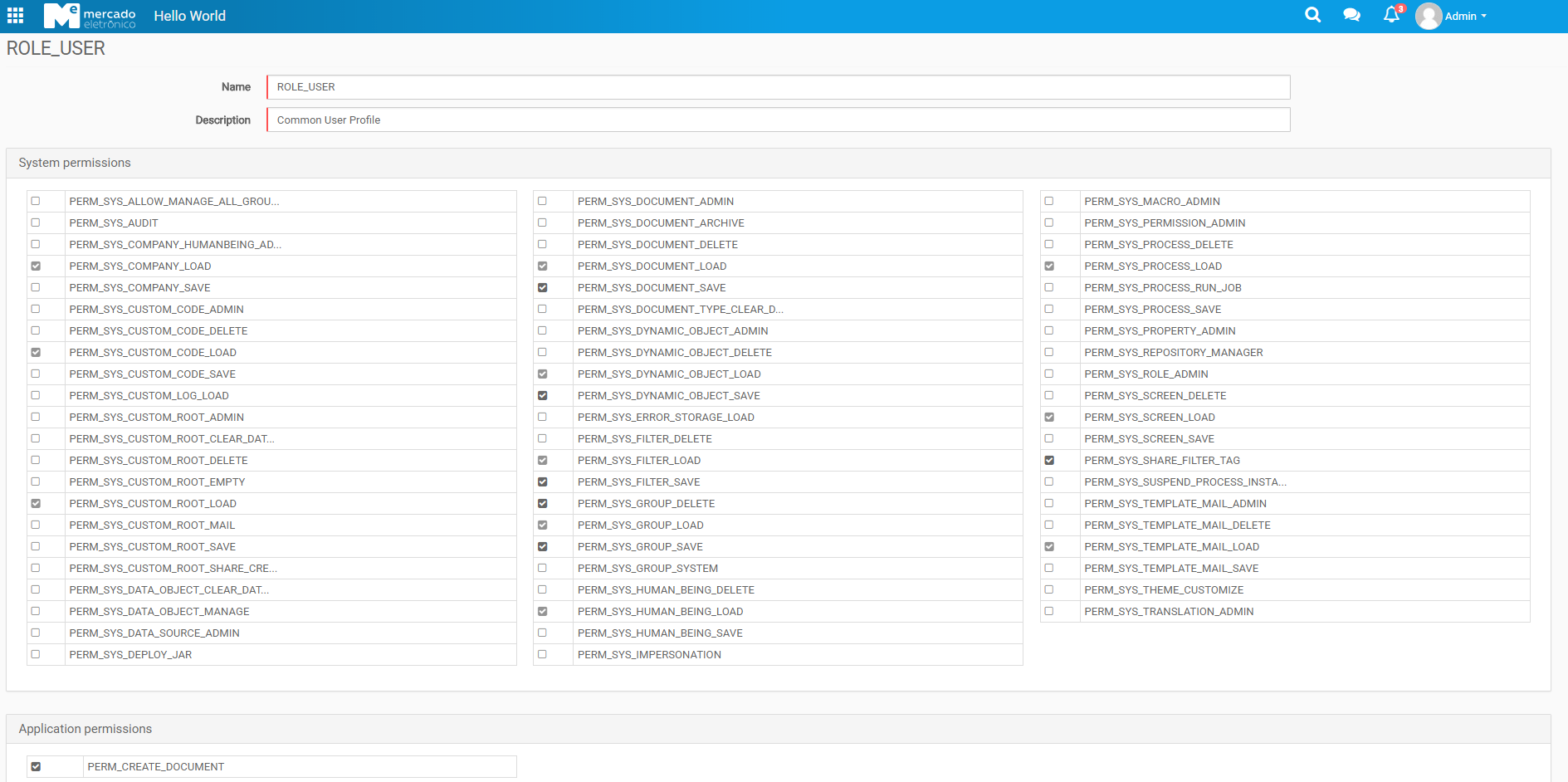
Method Security
- @RolesAllowed
Specified by JSR 250 (Java Specification Requests), this annotation specifies the list of roles permitted to access method(s) in an application. The value of the RolesAllowed annotation is a list of security role names. This annotation can be specified on a class or on method(s). More Details
- @Secured
Framework Spring Security original annotation.
From version 2.0 onwards Spring Security has improved support substantially for adding security to your service layer methods. It provides support for JSR-250 annotation security as well as the framework’s original @Secured annotation. For more details about Method Security here.
Example:
@RolesAllowed("PERM_NAME")
Register App.xml file
Roles and Permissions must be added to the App.xml file.
Example:
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<ns2:configuration xmlns:ns2="http://meceap.me.com.br/schema/config-mapping">
<roles>
<role name="ROLE_ADMIN" description="Administration Profile">
<permission name="PERM_CREATE_DOCUMENT" description="Allow documents creation"/>
</role>
</roles>
</ns2:configuration>
Best Practices
- @RolesAllowed in Controller and Manager: This is to ensure both application and integration.
- Create a new class AccessPermission with Constants: Default to use constants for the permission name.
- Use always "PERM_": As a prefix of the permission name, 'because?' can be seen here.
Example:
public class YourController {
@RolesAllowed(AccessPermission.PERM_CREATE_DOCUMENT)
public void create() {
}
}
public class AccessPermission {
@SimpleLabel("security.homologationCreate.manager")
public static final String PERM_CREATE_DOCUMENT = "PERM_CREATE_DOCUMENT";
}
For actions that are available to different roles but behave differently according to the role, use HumanBeingService. Example:
@Inject
private HumanBeingService humanBeingService
@URLUsedInBinding
@GetMapping("/{categoryId}/edit")
public ModelAndView method() {
boolean hasPermissionToEditCategory = humanBeingService.userPrincipalHasPermission(AccessPermission.EDIT_CATEGORY);
return new ModelAndView(new PageView(categoryId, hasPermissionToEditCategory));
}
- Never check Role name: Do not use the role name in code logic.
URL Security
When add @RolesAllowed on the Controller Class, the Spring create automatically an method on the Class "YourControllerSecurity".
Example:
public class YourControllerSecurity {
/**
* Check if the action create can be accessed by logged user according to Roles (Principal).
* See {@link meceap.yourProject.controller.YourController#create create method}.
*/
public static Boolean canCreate() {
try {
br.com.me.ceap.web.security.SpringSecurityValidator.validate(
meceap.yourProject.controller.YourController.class.getDeclaredMethod("create", new Class[0])
);
return true;
} catch (org.springframework.security.access.AccessDeniedException e) {
return false;
} catch (org.springframework.security.authentication.InsufficientAuthenticationException e) {
return false;
} catch (java.lang.NoSuchMethodException e) {
return false;
}
}
}
Spring Security
In MECEAP the Spring Security framework is used to control logged in users, authentications, authorizations, etc ... an introduction detailed can be seen here.
Role Anonymous
This Role is used to control users not logged on the System. For example in cases of the access via web service, consumes services, URLs specifies, etc... Spring Security’s anonymous authentication just gives you a more convenient way to configure your access-control attributes For more informations, look this documentation of the Spring Security Anonymous Configuration
Web Security
This is an Spring Security implementation, documentation about Web Security is here , bellow is an example of the an Web Security configured in MECEAP:
@Configuration
@EnableWebSecurity
public class SecurityConfiguration extends WebSecurityConfigurerAdapter {
@Value("${meceap.customRoot.name}")
private String customRootName;
protected void configure(HttpSecurity http) throws Exception {
http
.authorizeRequests()
.antMatchers("/"+customRootName+"/do/attachment/download/*").access("isAnonymous()")
.antMatchers("/"+customRootName+"/do/**").authenticated();
}
}
- App.xml file.
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<ns2:configuration xmlns:ns2="http://meceap.me.com.br/schema/config-mapping"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://meceap.me.com.br/schema/config-mapping http://docs.miisy.me/xsd/config-mapping.xsd">
<roles>
<role name="ROLE_ANONYMOUS" description="Anonymous User Profile"/>
</roles>
</ns2:configuration>